Phishing APIs For
Security Companies
Phishing APIs For
Security Companies
Phishing APIs For
Security Companies
Rapid, high confidence detection of malicious sites. Our automated analysis tools and let you find and neutralise sites faster with more confidence.
Rapid, high confidence detection of malicious sites. Our automated analysis tools and let you find and neutralise sites faster with more confidence.
Rapid, high confidence detection of malicious sites. Our automated analysis tools and let you find and neutralise sites faster with more confidence.
Get Started
Get Started
Get Started



Detect phishing kit TTPs
Detect phishing kit TTPs
Detect phishing kit TTPs
Classify known phishing kits and discover new variants
Classify known phishing kits and discover new variants
Classify known phishing kits and discover new variants
Our threat intelligence ruleset detects hundreds of technical indicators of phishing sites. From obfuscation techniques to C2 protocols, our ruleset accurately detects and identifies the techniques used by threat actors.
Our threat intelligence ruleset detects hundreds of technical indicators of phishing sites. From obfuscation techniques to C2 protocols, our ruleset accurately detects and identifies the techniques used by threat actors.
Our threat intelligence ruleset detects hundreds of technical indicators of phishing sites. From obfuscation techniques to C2 protocols, our ruleset accurately detects and identifies the techniques used by threat actors.
Millions of domains scanned every day. Our rule engine can scan millions of websites a day, returning a high accuracy verdict in milliseconds.
Millions of domains scanned every day. Our rule engine can scan millions of websites a day, returning a high accuracy verdict in milliseconds.
Rapid alerts. As soon as a new site matches signatures for your brand, we alert you—usually within minutes of them being created.
Rapid alerts. As soon as a new site matches signatures for your brand, we alert you—usually within minutes of them being created.
Tuning help from our detection engineers. Our phishing experts are available to help you tune your rules and write new ones.
Tuning help from our detection engineers. Our phishing experts are available to help you tune your rules and write new ones.
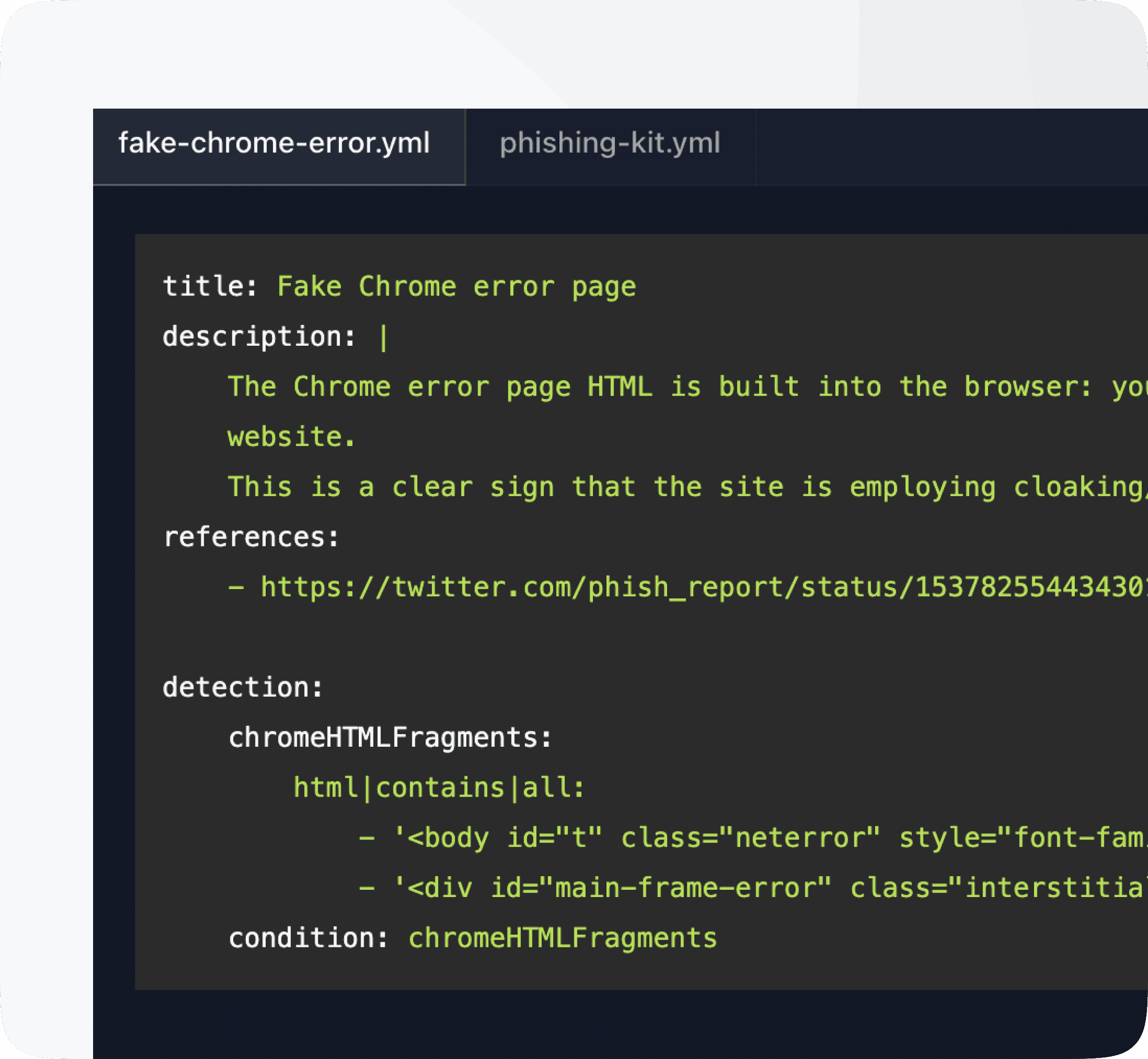

Phishing Firehose
Phishing Firehose
Phishing Firehose
Unleashing the Power of TTP Detection
Unleashing the Power of TTP Detection
Unleashing the Power of TTP Detection
We're boiling the ocean to get all phishing urls even from the hardest to find places by focusing on Phishing TTPs rather than brand detection and machine vision. It's a different approach
We're boiling the ocean to get all phishing urls even from the hardest to find places by focusing on Phishing TTPs rather than brand detection and machine vision. It's a different approach
We're boiling the ocean to get all phishing urls even from the hardest to find places by focusing on Phishing TTPs rather than brand detection and machine vision. It's a different approach
TTP Focus, we analyze the methods employed by phishing actors. By understanding their playbook, we can anticipate their next moves and proactively block malicious URLs before they can do any damage.
TTP Focus, we analyze the methods employed by phishing actors. By understanding their playbook, we can anticipate their next moves and proactively block malicious URLs before they can do any damage.

Request a Demo
Get Started
Request a Demo
Get Started
Request a Demo
Get Started
Twitter / X
Products
Company
© 2024 InterceptIO, Inc. All rights reserved.
Twitter / X
Products
Company
© 2024 InterceptIO, Inc. All rights reserved.
Twitter / X
Products
Company
© 2024 InterceptIO, Inc. All rights reserved.
